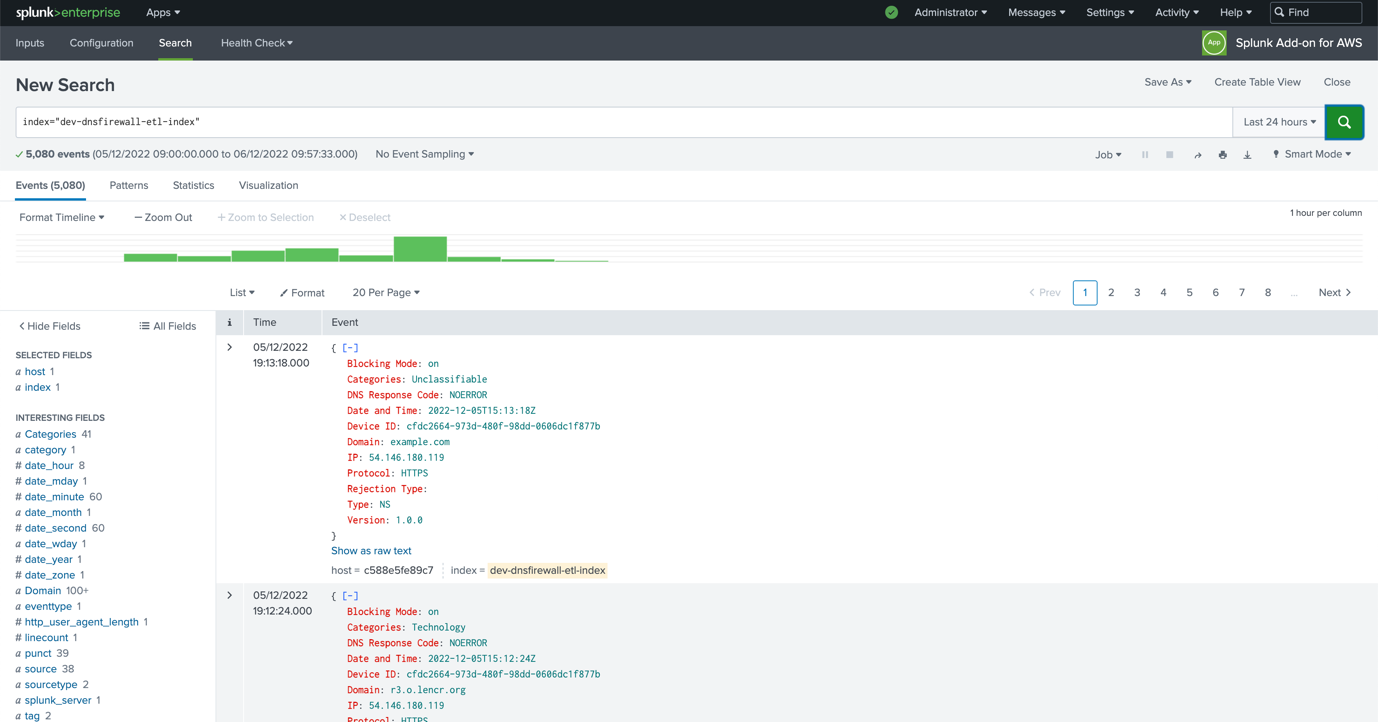
Splunk integration
This guide lists the steps to configure Splunk to ingest CSV. With our Data Export feature, you can directly import DNSFirewall data to all SIEMs that have integration with AWS S3.
SIEM integration and configuration stages mentioned below are specific to the SPLUNK (SIEM) Environment. Splunk is a Unified Security and Observability Platform. It enables end-to-end visibility of your DNS requests.
Search your data
Explore data of any type and value — no matter where it lives in your data ecosystem.
Analyze your data
Drive business resilience by monitoring, alerting, and reporting on your operations.
Visualize your data
Create custom dashboards and data visualizations to unlock insights from anywhere — in your operations center, on the desktop, in the field and on the go.
Act on your data
Use data from anywhere across your entire organization so you can make meaningful decisions fast.
SPLUNK CONFIGURATION
Data ingest configuration to the Splunk will run through following stages.
- To collect data from an S3 bucket, we’ll first need to install the Splunk Add-on for Amazon Web Services. This generally should be installed on a Heavy Forwarder.
- Once the app is installed, you’ll want to launch the app to configure the IAM user and role.
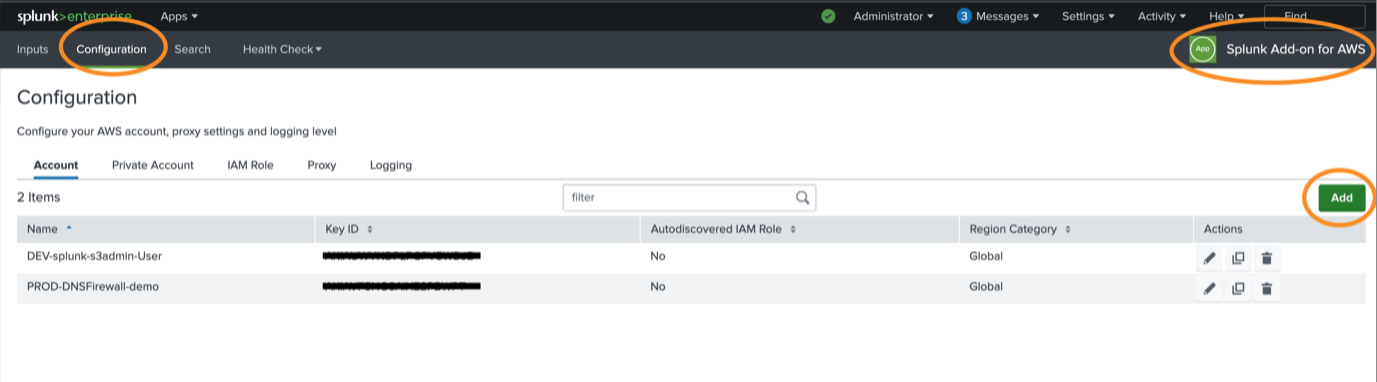
 3. The accounts in the AWS Add on are configured under Configuration -> Account in the app. Click Add to add a new account.
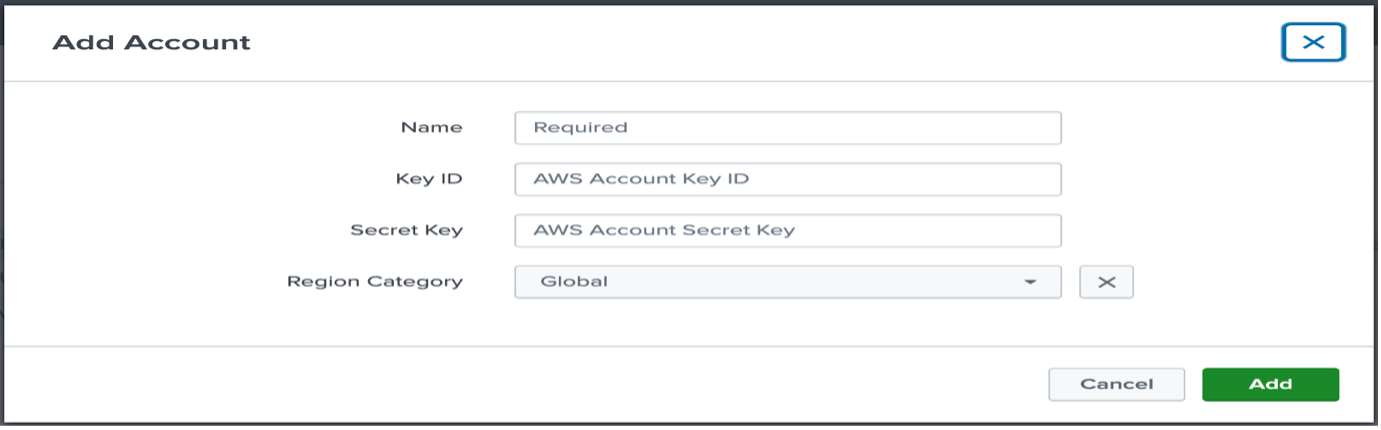
In the Add Account screen, provide the name of the account, Key ID, and Secret Key for the IAM user you created above.
Once this account is added, you’ll see it in the list of accounts:
3. The accounts in the AWS Add on are configured under Configuration -> Account in the app. Click Add to add a new account.
In the Add Account screen, provide the name of the account, Key ID, and Secret Key for the IAM user you created above.
Once this account is added, you’ll see it in the list of accounts:
- Configure an S3 Input There are two ways to configure an S3 input: through the AWS Add-on or through the Data inputs menu in settings. For this example, we will navigate to Splunk Add-on for AWS -> Inputs -> Create New Input.
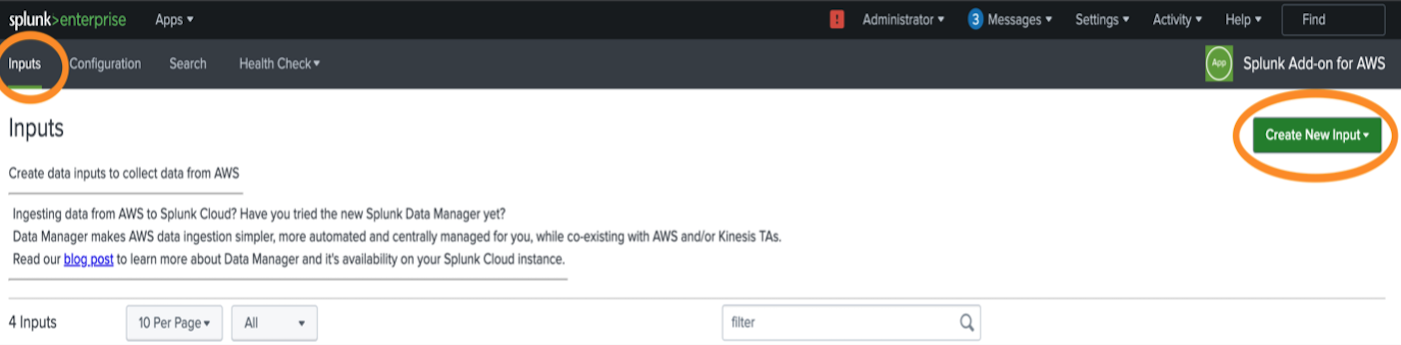
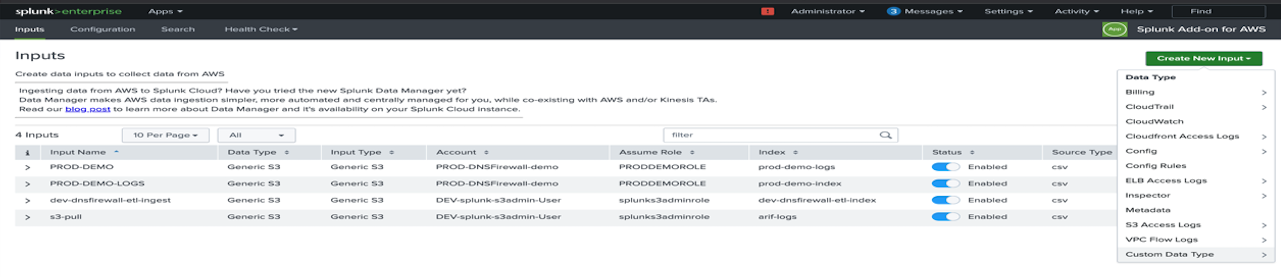
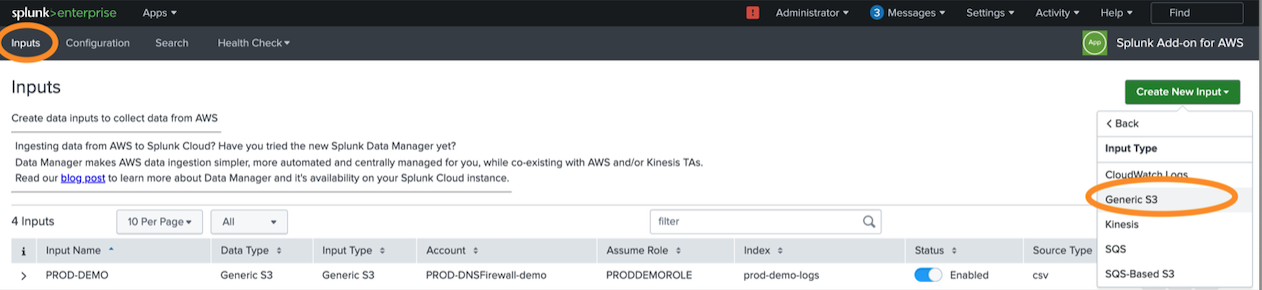
4.1. Select the “Custom Data Type” -> Generic S3
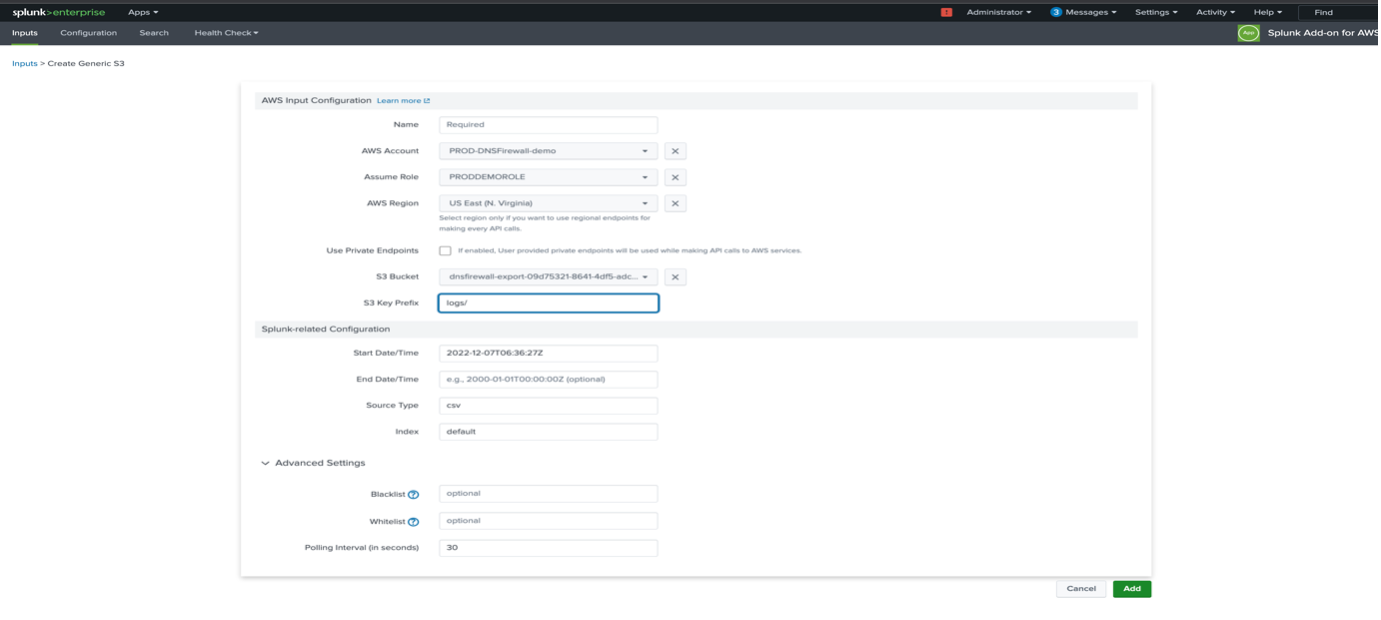
4.2. Configure the settings for your input. For this example, the Name, AWS Account (matching the account specified in the AWS Add-on), and Bucket Name (matching the name of the bucket in S3), as well as the Index where the data will be stored are prefilled.
4.3. Select data type as “CSV”.
- Configure the ingest search.